My Experience Presenting at WLPC Valencia 2025

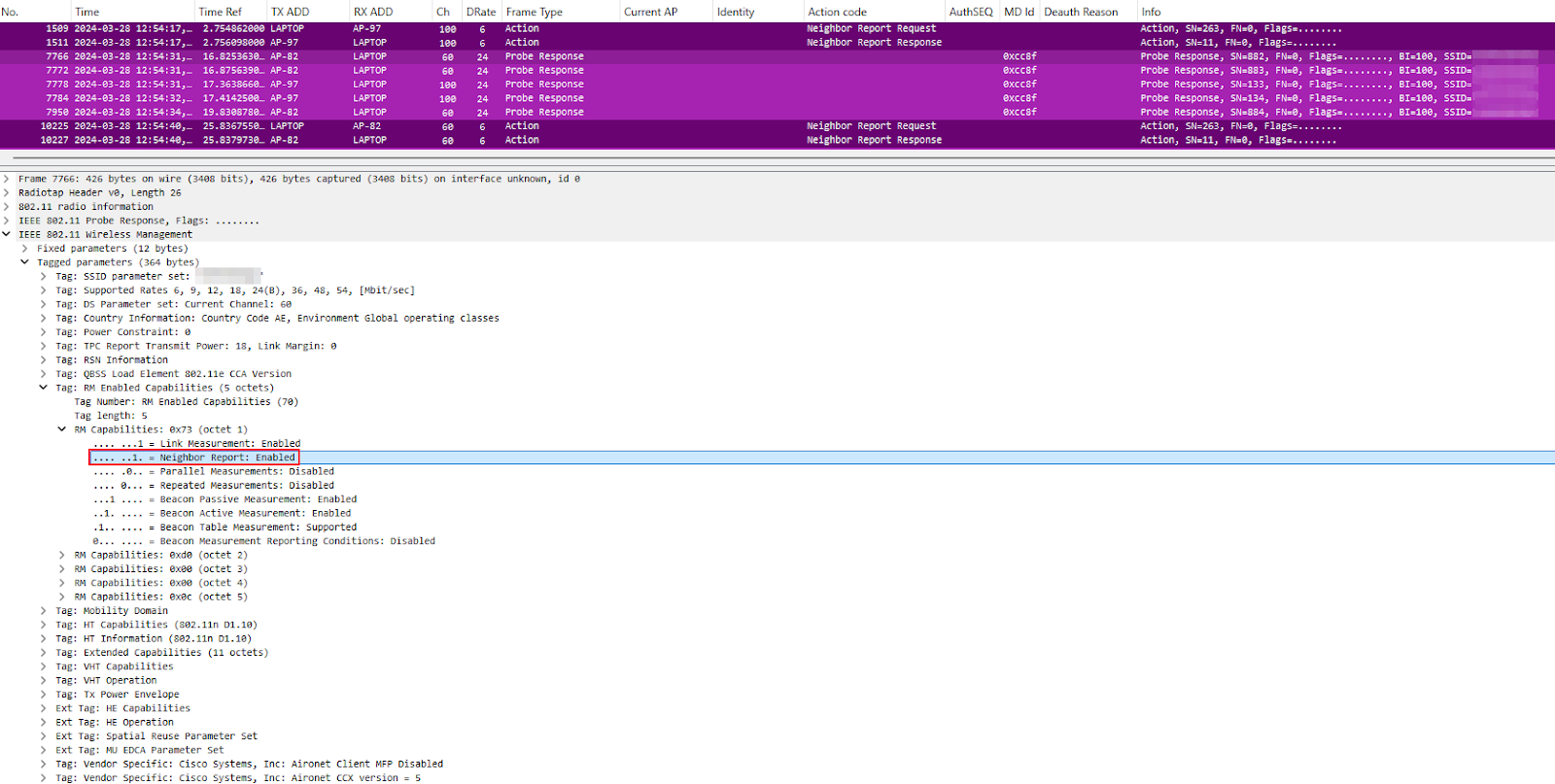
My Experience Presenting at WLPC Valencia 2025 Hello everyone. Following the recent WLPC Valencia 2025 event, I want to share some critical pedagogical insights gained from teaching a Deep Dive session on Wireshark Capture Analysis. The conference itself was invaluable, offering expert-level content covering the latest in Wi-Fi 7 (802.11be), Multi-Link Operation (MLO), essential tools like Hamina and Sidos, Troubleshooting with Checklists and Applying AI in Network Operations. However, the most profound learning experience for me was the process of translating advanced, practical knowledge into a structured classroom environment. The Initial Miscalculation of Scope To be completely honest, the timing of WLPC this year was highly unfavorable due to demanding personal and professional commitments. This resulted in severely constrained time for preparing the class content—and virtually no time for practicing the lecture delivery. I developed a dangerous misconception: given the high calib...